The Korean government has a free service for scanning the dark web and related personal account information leaks, to see if any of your account logins have been revealed in any known leaks. The service is similar to the "Have I Been Pwned?" website popular in the English speaking internet. In Korean it is known as the "털린 내 정보 찾기 서비스."
Using it is surprisingly simple, and only requires an active e-mail address to verify your use of the service, which itself is deleted every night. Here's how it works.
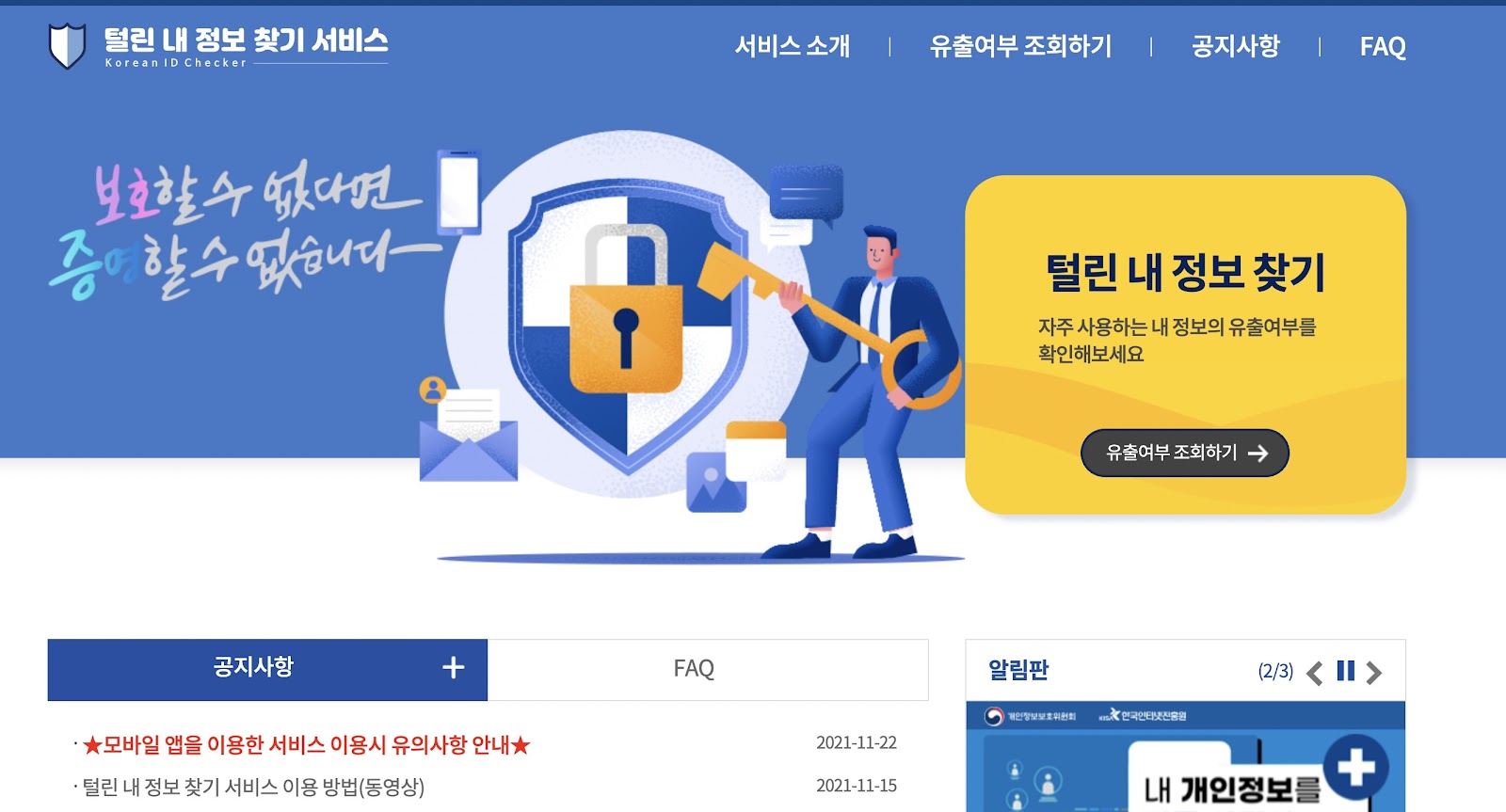 |
| Korean logins checking service. Image: KIDC |
First, visit the website at https://kidc.eprivacy.go.kr/
Click the giant yellow banner as shown above. Or go directly to the sign-up page here: https://kidc.eprivacy.go.kr/search/issueVerify.do
You'll be brought to a page that explains the process.
As it explains, and in the FAQs, you will be inputting up to 5 logins (usernames and passwords) for accounts you may want to check.
I think the point of this is that so many people reuse the same usernames/password combination on multiple sites. For example, you might have the @10wontips Twitter handle, be 10wontips@gmail.com, onlyfans.com/10wontips (ha ha), and reuse the same password for all. So the page isn't asking you for specific websites where you have accounts. It simply wants your commonly used usernames and passwords commonly used with those usernames.
Obviously this seems like a security risk to just give your login IDs/passwords here, but the page says all inputted information is hashed and destroyed near immediately after comparing your inputted data with their saved database of known leaks, including dark web leaks. Up to you if you trust this or not, but considering how often I've seen people reuse logins and passwords, and never use a password manager, it's probably not any riskier than their current online security habits.
Moving on. At the bottom of the page there's a box where you input your email address( USER @ SITE.COM) and hit the gray button to send a verification email to you, just to prove that you are real.
Put that code into the second box under where you input your email and hit the blue button. You'll then have the right-side of the box activated with a simple CAPCHA checkbox to click.
Now you'll be at the page to input your usernames and passwords. Pretty obvious where they go.
It will run an immediate scan when you click the red 확인 (confirm) button, and hopefully all the results will return green. If anything comes back red, it's a known leak and you really ought to change that password anywhere you use it.
 |
| Image: ZDnet Korea |
If you get a red result, you can click through to get more info on where the leak is known from, but I didn't get any reds so can't verify that.



Comments